
ConfigBytes: ASA 5506x w/ FirePOWER Services
#ConfigBytes
Getting Started with the ASA5506x & FirePOWER Services
http://www.cisco.com/c/en/us/td/docs/security/asa/quick_start/5506X/5506x-quick-start.html
FirePOWER Services for ASA Data Sheet:
TL:DR Key Points
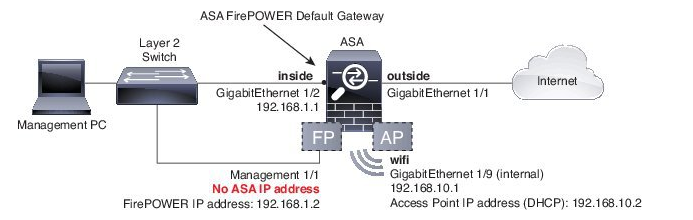
- Since the ASA5506x doesn’t have built-in switch capabilities (yet), you will need a L2 switch to connect the management interface which is used for firepower services module and your inside ASA interface for management. If you have an L3 switch the FirePOWER management interface can be on a different subnet from your inside ASA interface.
- Download ASDM 7.4(3)image, ASA 9.4(1)3 and the latest firepower/sourcefire sensor patch (5.4.1.2 at this time). Place these files on the ASA flash, upgrade and point to the new ASDM file.
- Create a username/password w/ PRIV 15 for ASDM access. “username Wu-Tang password KillaBeesOnTheSwarm privilege 15”
- I highly recommend using the ASA Startup Wizard, this is much easier then a console session (“session srf console”) to the FirePOWER services module for setup of management.
- Default Username/Password for the SourceFIRE module is admin/Sourcefire
- Upgrade FirePOWER through ASDM or FireSight. Remember you can use ASDM or FireSight to manage the FirePOWER services.
- Install your FirePOWER licenses
- Don’t forget to configure a service policy on the ASA to redirect traffic to the FirePOWER module.
Final Config
5506xFPS(config)# sh run
: Saved
: Serial Number: <removed>
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.4(1)3
!
hostname 5506xFPS
domain-name cisco.lab
enable password <removed>
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address dhcp setroute
!
interface GigabitEthernet1/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
description Inside_2
nameif inside2
security-level 100
ip address 10.100.220.1 255.255.255.0
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
boot system disk0:/asa941-3-lfbff-k8.SPA
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns server-group DefaultDNS
domain-name cisco.lab
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
pager lines 24
logging enable
logging buffer-size 8192
logging asdm-buffer-size 250
logging console emergencies
logging asdm alerts
mtu outside 1500
mtu inside2 1500
icmp unreachable rate-limit 1 burst-size 1
icmp deny any outside
asdm image disk0:/asdm-743.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
nat (inside2,outside) after-auto source dynamic any interface
route inside2 10.0.0.0 255.0.0.0 10.100.220.2 1
route inside2 172.16.0.0 255.240.0.0 10.100.220.2 1
route inside2 192.168.0.0 255.255.0.0 10.100.220.2 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
user-identity default-domain LOCAL
http server enable
http 10.100.220.0 255.255.255.0 inside2
no snmp-server location
no snmp-server contact
sysopt noproxyarp outside
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=10.100.220.1,CN=5506xFPS
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpoint ASDM_TrustPoint0
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
<removed>
quit
telnet timeout 5
ssh scopy enable
ssh stricthostkeycheck
ssh pubkey-chain
server 10.100.220.153
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd address 10.100.220.10-10.100.220.199 inside2
dhcpd dns 216.144.187.199 8.8.8.8 interface inside2
dhcpd lease 28800 interface inside2
dhcpd enable inside2
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
ntp server 129.6.15.30 source outside prefer
dynamic-access-policy-record DfltAccessPolicy
username asa password encrypted privilege 15
username admin password encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
class-map global-class-SF
match any
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
description Global+SF
class global-class-SF
sfr fail-close
class inspection_default
inspect dns preset_dns_map
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly 8
subscribe-to-alert-group configuration periodic monthly 8
subscribe-to-alert-group telemetry periodic daily
hpm topN enable
Cryptochecksum:8c074bd2be57c9a8df6e364e77b07ae7
: end
Video Example of URL Filtering with FirePOWER
https://youtu.be/OAdGZliSC34
2 thoughts on “ConfigBytes: ASA 5506x w/ FirePOWER Services”
Great post!
I was able to install and setup firepower. However I don’t see button to create new policy under Configuration->Asa Firepower configuration->Access policy. I have only default policy. Any thoughts? I have control and malware license applied. Running asa version 9.5(1)5, firepower 6 and asdm 7.5(2)
Thanks
Thanks for the feedback! Did you configure the service policy to redirect the traffic to the firepower module?
Procedure
1. To send traffic to the module, choose Configuration > Firewall > Service Policy Rules.
2. Choose Add > Add Service Policy Rule.
3. Choose whether to apply the policy to a particular interface or apply it globally and click Next.
4. Configure the traffic match. For example, you could match Any Traffic so that all traffic that passes your inbound access rules is redirected to the module. Or, you could define stricter criteria based on ports, ACL (source and destination criteria), or an existing traffic class. The other options are less useful for this policy. After you complete the traffic class definition, click Next.
5. On the Rule Actions page, click the ASA Firepower Inspection tab.
6. Check the Enable ASA Firepower for this traffic flow check box.
7. In the If ASA Firepower Card Fails area, click one of the following:
– Permit traffic —Sets the ASA to allow all traffic through, uninspected, if the module is unavailable.
– Close traffic —Sets the ASA to block all traffic if the module is unavailable.
8. (Optional) Check Monitor-only to send a read-only copy of traffic to the module, i.e. passive mode.
9. Click Finish and then Apply.
Repeat this procedure to configure additional traffic flows as desired.
Comments are closed.