KRACK
(K)ey (R)einstallation (A)tta(C)(K)
Breaking WPA2 by forcing nonce reuse
It’s been a long day and I wanted to have some fun with this post. I was onsite with several customers today when the news broke publicly. I only knew about it at a high-level in the morning and didn’t have time to digest the magnitude nor details of the vulnerability until this evening.
You see, for me this feels somewhat like Deja Vu. I remember the day when it was discovered that WEP had a key weakness in its security algorithm. That weakness was simple. Collect enough 3 Byte Initialization Vectors (IVs) that are transmitted in clear text and you could use commercial off the shelf hardware (Atheros chipset) and software (BackTrack now known as Kali Linux/aircrack-ng/JTR) to crack the key. It’s was stupid simple to execute this attack and ultimately was the demise of WEP.
Fast forward 11+ years and here we are talking about another major vulnerability affecting pretty much EVERY wireless network deployed. The saving grace… This is NOWHERE near as bad as the WEP exploit and can be fixed.
Just the Facts
- The proof-of-concept exploit is called KRACK, short for Key Reinstallation Attacks.
- Directly attacks the 4-way handshake used by the WPA (802.11i) protocol.
- The research has been a closely guarded secret for weeks ahead of a coordinated disclosure that was scheduled for 8am Monday (10.16.2017), East Coast time.
- Discovered by Mathy Vanhoef of imec-DistriNet, KU Leuven
- Full post and deep dive by Mathy available here
- Affects WPA/WPA2/personal (PSK) and enterprise as well as ALL ciphers (WPA-TKIP, AES-CCMP, and GCMP)
- All of the CVEs are related to the supplicant (client) with only one exception (CVE-2017-13082) that directly impacts the authenticator (AP/infrastructure).
- CVE-2017-13077 CVE-2017-13078 CVE-2017-13079 CVE-2017-13080 CVE-2017-13081 CVE-2017-13082 CVE-2017-13084 CVE-2017-13086 CVE-2017-13087 CVE-2017-13088
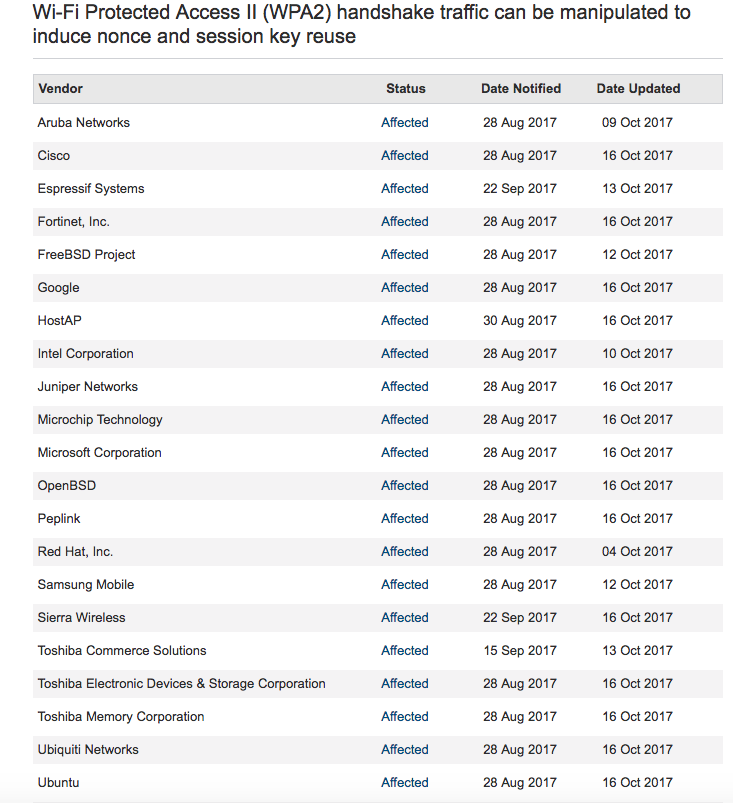
- Affects multiple Vendors (see inline)
- Specifically related to Cisco. See this link for full details along with affected products and patch information. https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171016-wpa
- Cisco Patch Update:
CSCvf47808 8.0.15x.0: ETA October 19th, 2017
8.2.16x.0: ETA October 20th, 2017
8.3.130.0: available now
8.5.10x.0: ETA October 20th, 2017
8.6.100.0: TBDCSCvg10793 8.2.16x.0: ETA October 20th, 2017
8.3.13x.0: ETA October 20th, 2017
8.5.10x.0: ETA October 20th, 2017
8.6.100.0: TBD - Meraki also did a great job updating customers with their blog and going as far to update the dashboard to show any vulnerable networks/devices.
- The attack DOES NOT expose passwords/PSKs.
Next Steps
- Keep checking back here for updates, especially if you are looking at Cisco infrastructure, available patches, and attack detection methods.
- Link to one of my colleagues (Gio) page on how to setup the WLC to detect an attack using best practices.
- Read the entire research paper if you want a deep dive on the attack. https://papers.mathyvanhoef.com/ccs2017.pdf
- Do we need WPA3? I don’t think so. It’s clear that much of this attack is focused on the implementation of the 802.11i standard. While it’s true that there was a protocol level exploit (802.11r FT), this was only one of the CVEs and can be patched.
- Don’t switch to WEP! 😉 Keep using WPA2 and patch accordingly.
- One interesting comment on the security researches (Mathy) page was the very last bullet point…
“So you expect to find other Wi-Fi vulnerabilities?”
I wholeheartedly agree with you Mathy!
-shaun